In the IdP environment, you must add Treasure Data to your list of authorized applications. Each Treasure Data account is added as a separate application and users are assigned to the Treasure Data applications in Okta.
Continue to the following topics:
- Prerequisites
- Create a Treasure Data Application in Okta
- Configure Okta in TD Console
- Create a Treasure Data Bookmark Application in Okta
- Application Username in Okta and User Identifier in TD Console
Treasure Data doesn't support the IdP-initiated SSO to ensure security. You cannot log in from the Treasure Data application (which you configured Single Sign-On URL, URI, etc), which is configured in Create a Treasure Data Application in Okta,You must log into [https://YOUR_TD_REGION/users/initiate_sso?account_name=ACCOUNT_NAME](<https://YOUR_REGION_TD.com/users/initiate_sso?account_name=ACCOUNT_NAME>) directly, or log in via Bookmark Application which is configured here Create a Treasure Data Bookmark Application in Okta
SSO account name
Okta Account
Treasure Data Account
URN resource
- After a new SSO-configured account has been set up for you by your account representative, create and set up a new application in Okta.
When the TD account is configured with the sso-configuration-enabled feature flag and given an account_name for IdP, a unique URN is created. You’ll need both the account_name for IdP and the supplied URN to configure your Okta account.
Log into your Okta account as an Admin and select the Admin button.
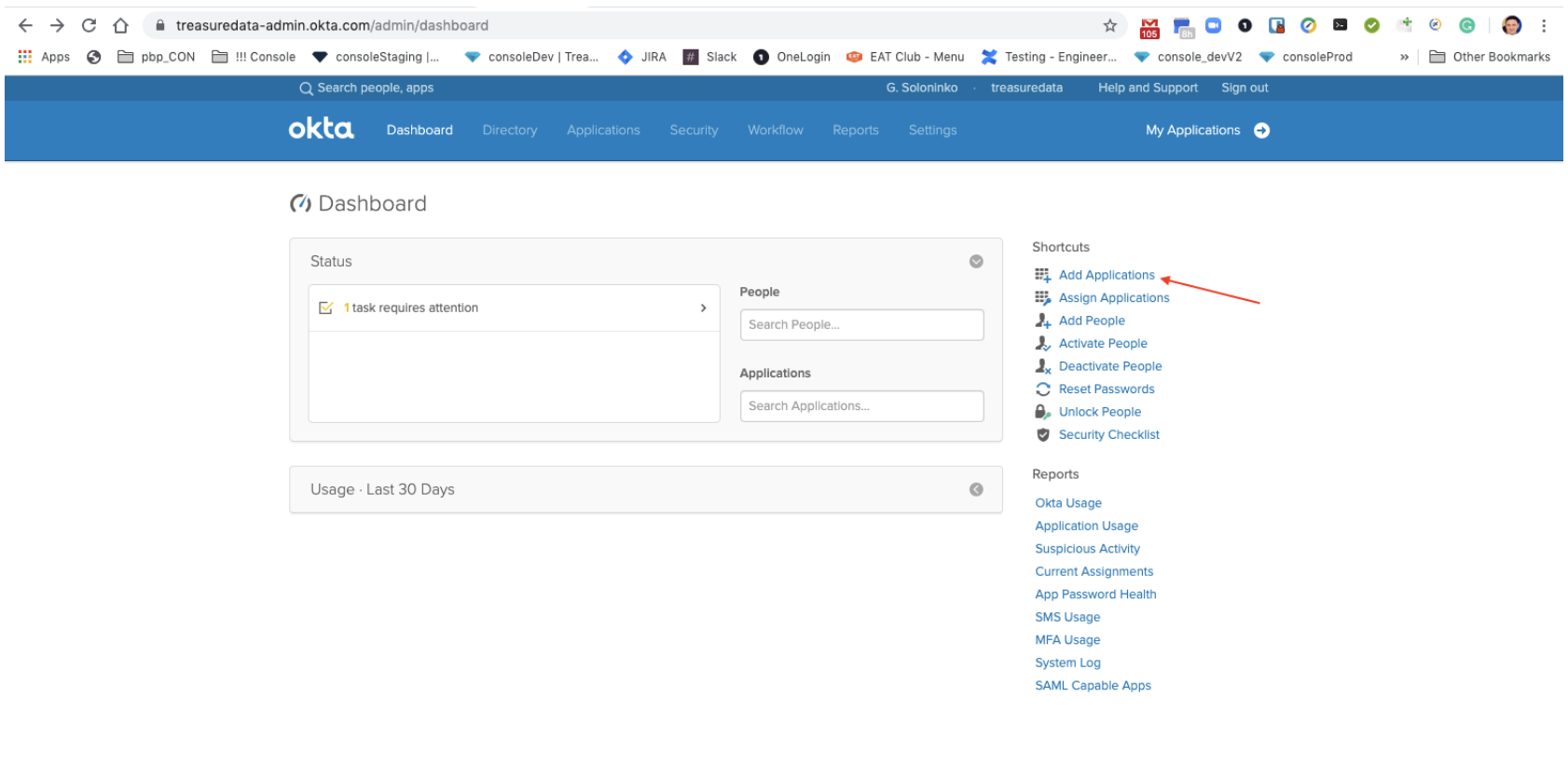
Select Add Applications.
Your screen might look like this depending on how you accessed your Okta account.
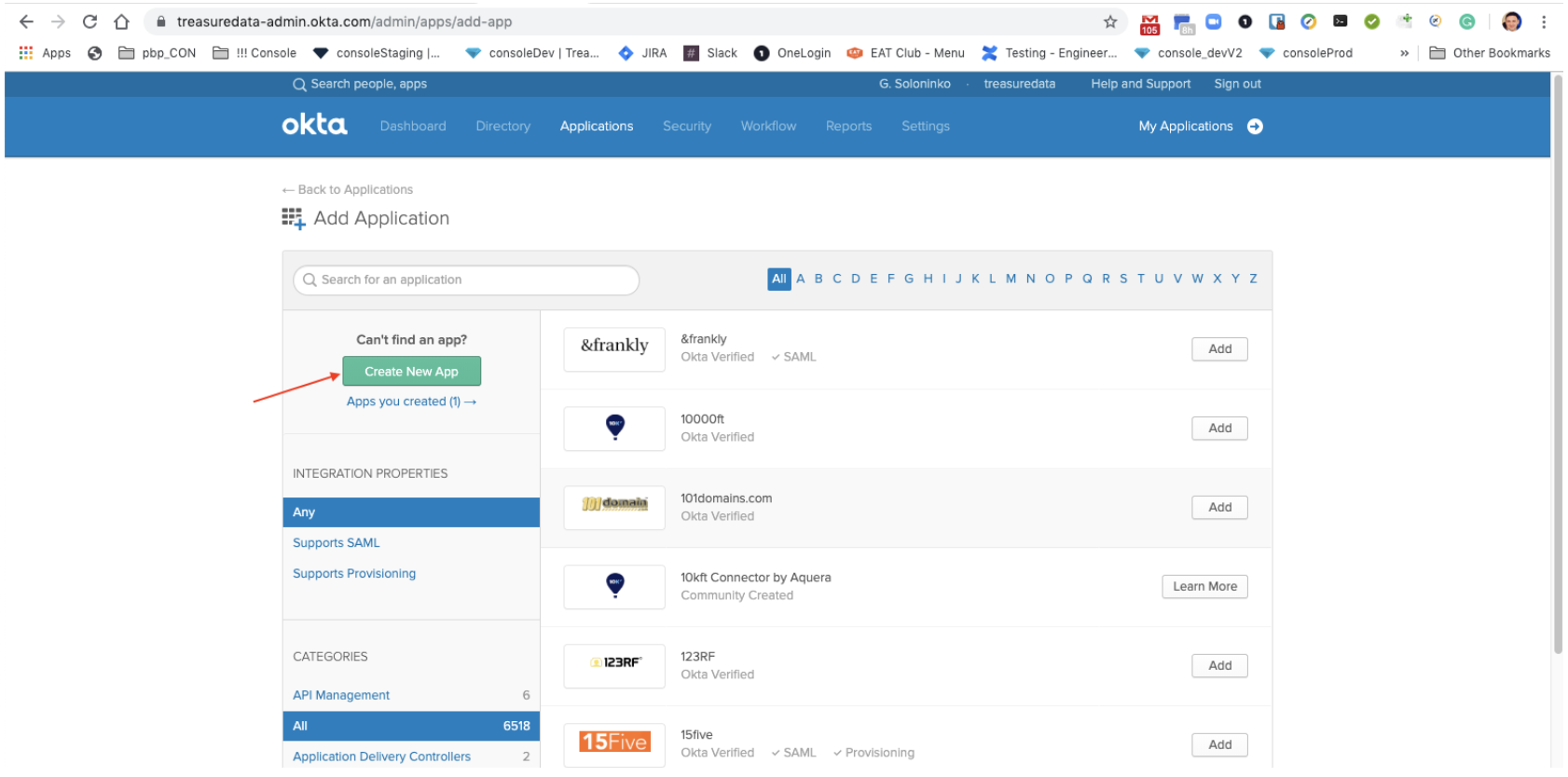
- Select Create New App.
Your screen might look like this.
- Next, select the SAML 2.0 protocol, which is used by Treasure Data to exchange authentication and authorization identities between security domains.
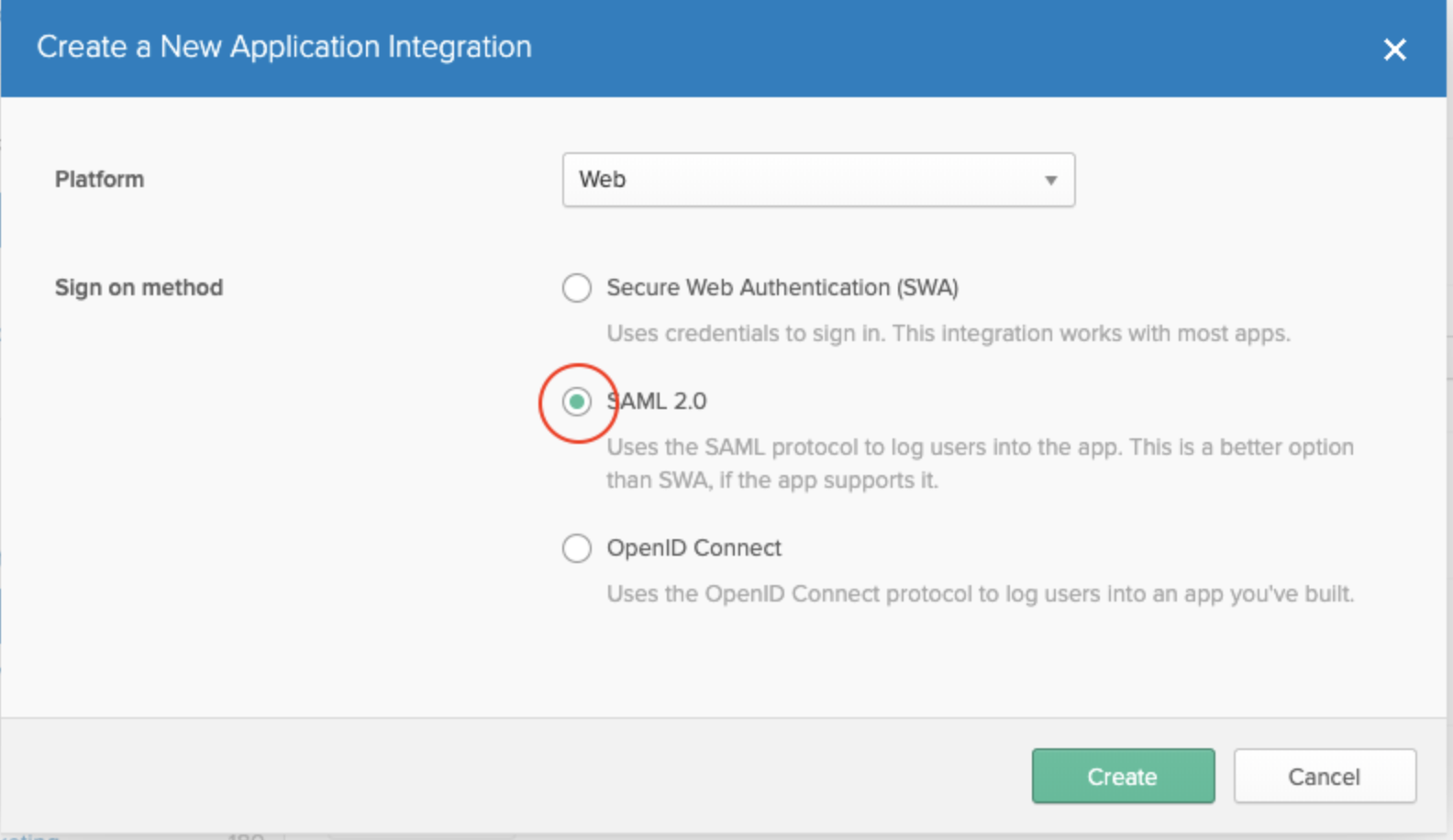
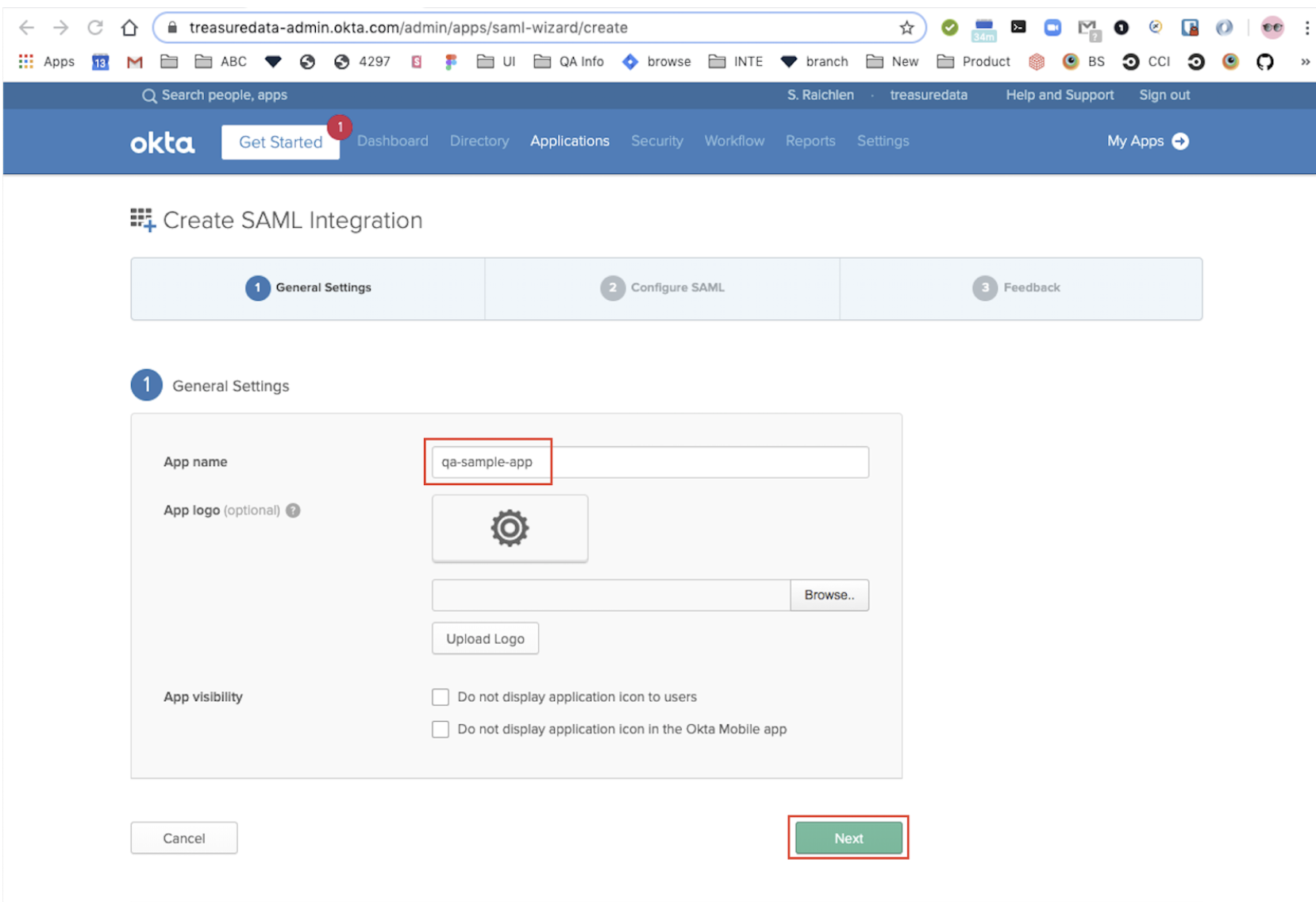
Configure SAML by typing in your App Name and uploading a logo if desired.
Set App visibility options:
Select:Do not display application icon to users
Select:Do not display application icon in the Okta Mobile appSelect Next.
Configure SAML.
Use
https://sso.treasuredata.com/login/callbackas your Single Sign-On URL. Note this value does not change in any sites or regions.Use the urn that was created when your TD account was configured
urn:treasuredata:sso:<SITE>:<ACCOUNT_NAME> as your Audience URI (SP Entity ID).
Where<SITE> is currently one of the following: aws, aws-tokyo, eu01, or ap02.
For example, urn:treasuredata:sso:eu01:ACCOUNT_NAME.
- Keep Default Relay State empty.
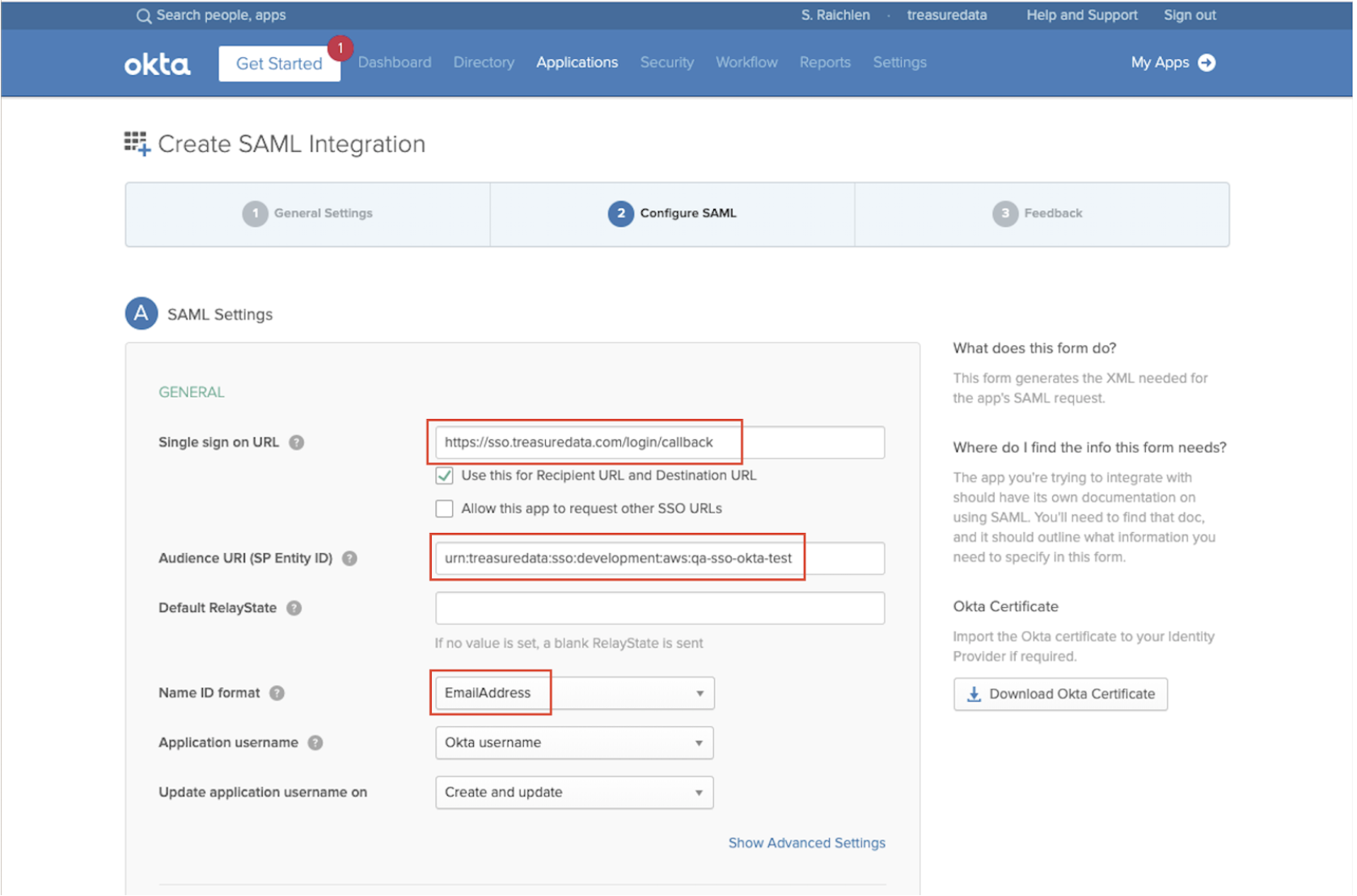
Select Next.
Select Directory and add or invite new user(s) by selecting Add Person.
- Specify the name and email of the user you wish to invite.
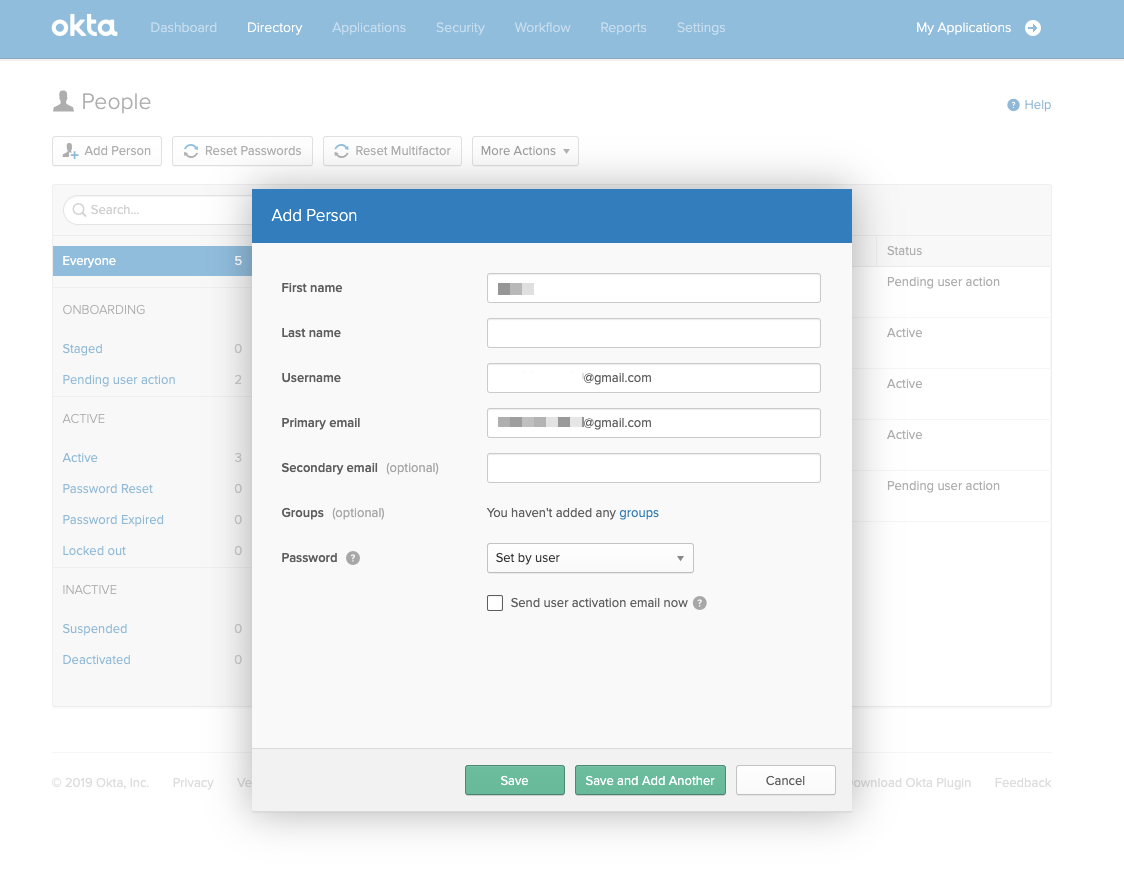 13. Select Save.
13. Select Save.
- Each invited user receives an email with the link to activate their account. You can view which invitations are active or still pending activation.
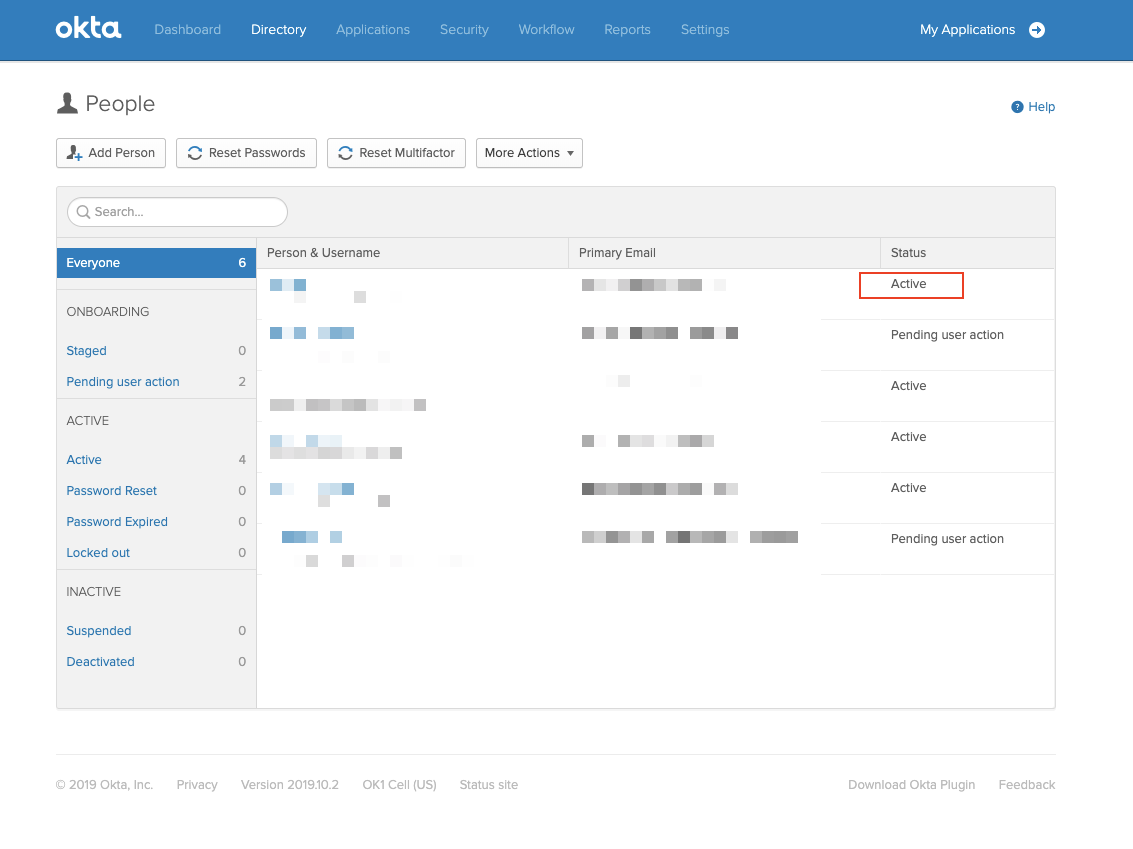
- Next, select Okta users to assign to your Okta application.
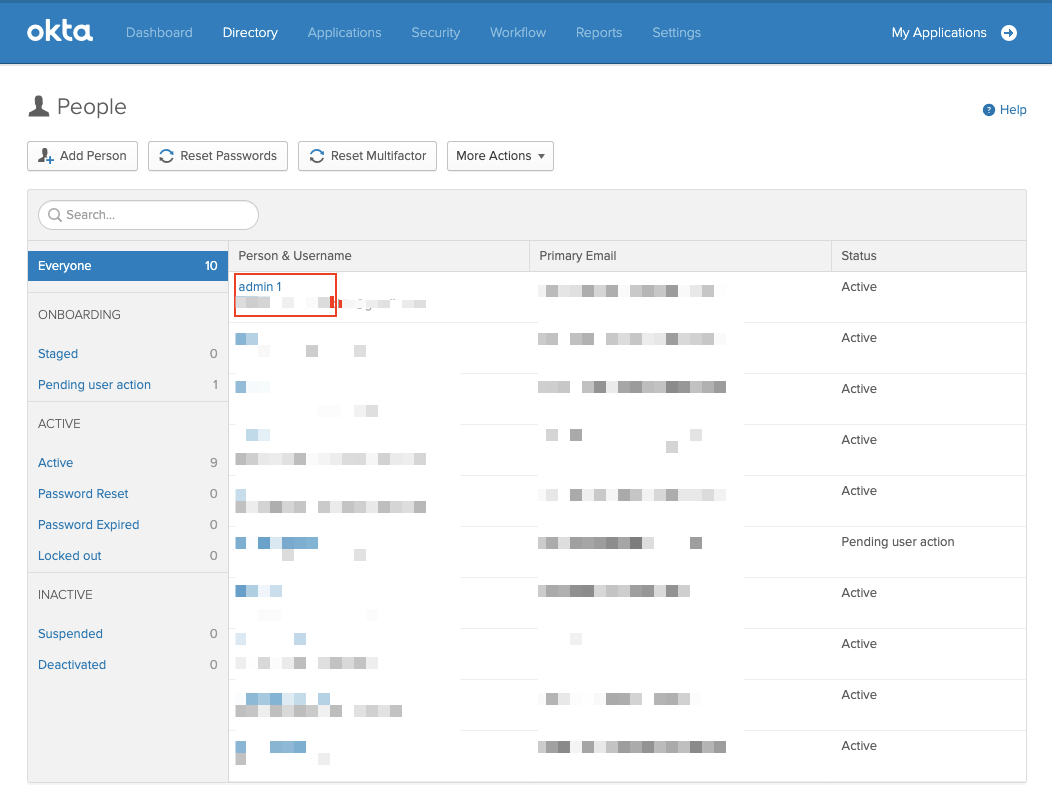
- Select Assign Applications.
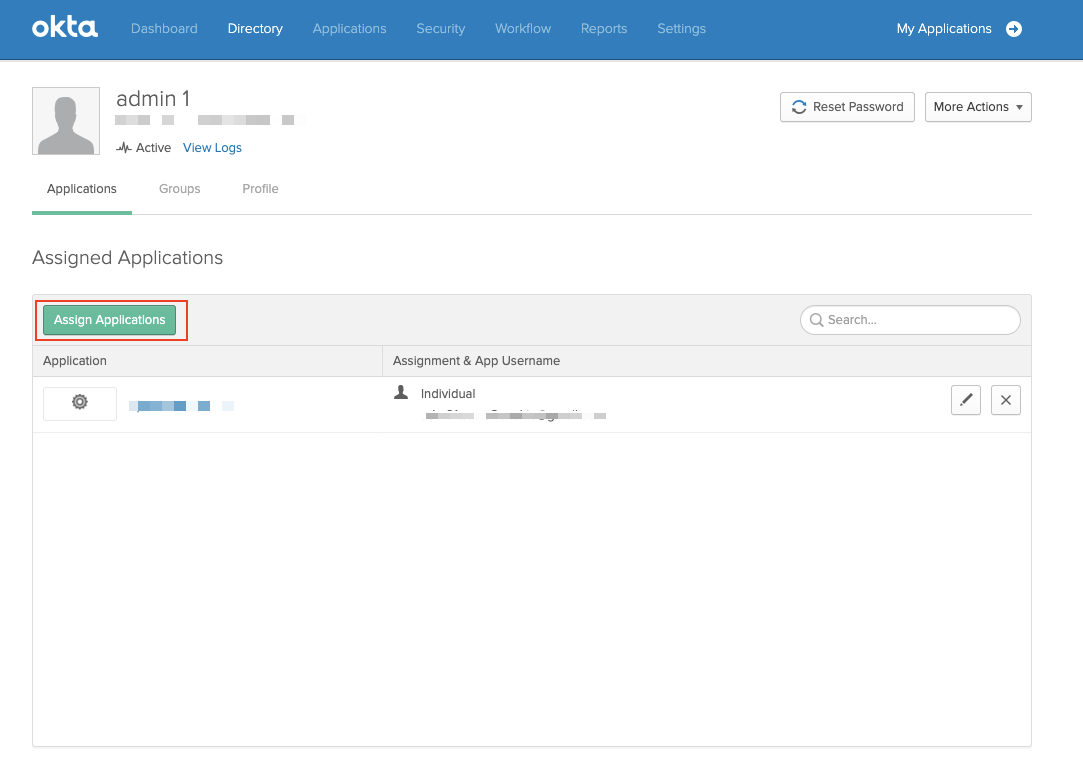
- Select Assign to add the user to the account.
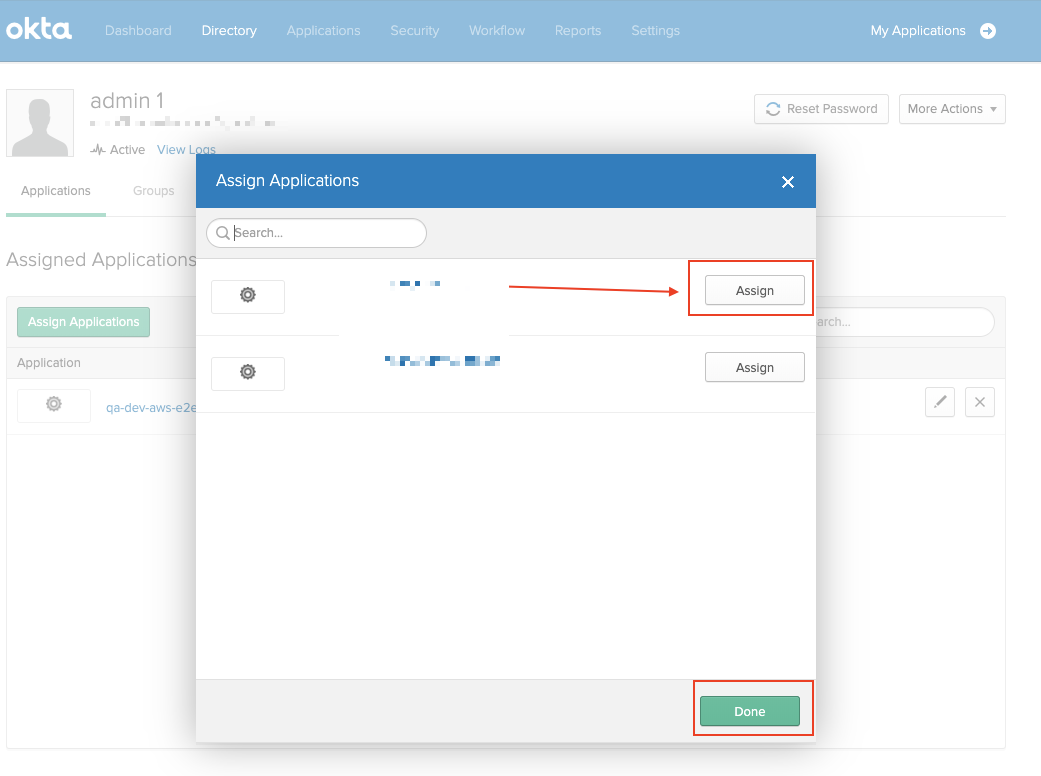
- After the user is added to Treasure Data as an Okta user, they are redirected to Okta and to present their Okta credentials for authentication. You can then harvest the configuration needed to configure the IdP for a Treasure Data account.
Select the app and select View Setup Instructions.
- Configure the Treasure Data account for this Okta application by collecting either of the following options and installing Treasure Data.
The Identity Provider Single Sign-On URL
X.509 Certificate
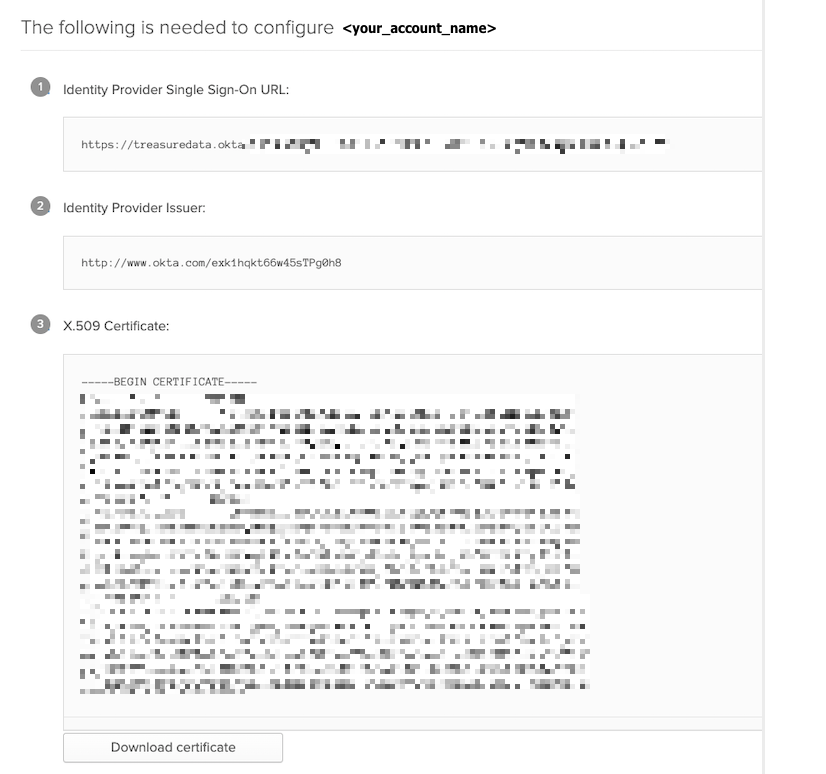 20. To enter the information using a single metadata file, copy the IDP metadata into a file and use it to configure the TD account.
20. To enter the information using a single metadata file, copy the IDP metadata into a file and use it to configure the TD account.

At this point, set up your configuration in TD Console.
Next, you can test your connection.
Optionally, you can complete your work in Okta before working in TD Console.To complete the configuration in Okta, proceed to the next step of creating a Bookmark Application in Okta.
Bookmark apps direct users to a specific web page using a small Okta icon or chiclet. The Bookmark App allows the user to sign in to the application directly—without providing sensitive credential information.
The following steps are based on instructions from the Okta help documentation.
Create and set up another application on Okta
Specify the App name. You can specify any bookmark name, such as Treasure Data SSO. The name you specify is viewable from the Okta dashboard.
Specify the SSO URL. The URL is
https://YOUR_REGION_TD/users/initiate_sso?account_name=ACCOUNT_NAME. For example, if you use prod-aws, the URL would be:https://console.us01.treasuredata.com/users/initiate_sso?account_name=ACCOUNT_NAME.
You obtain the account name from your Treasure Data customer success representative.
- Assign Okta users to your Okta application bookmark and test the connection.
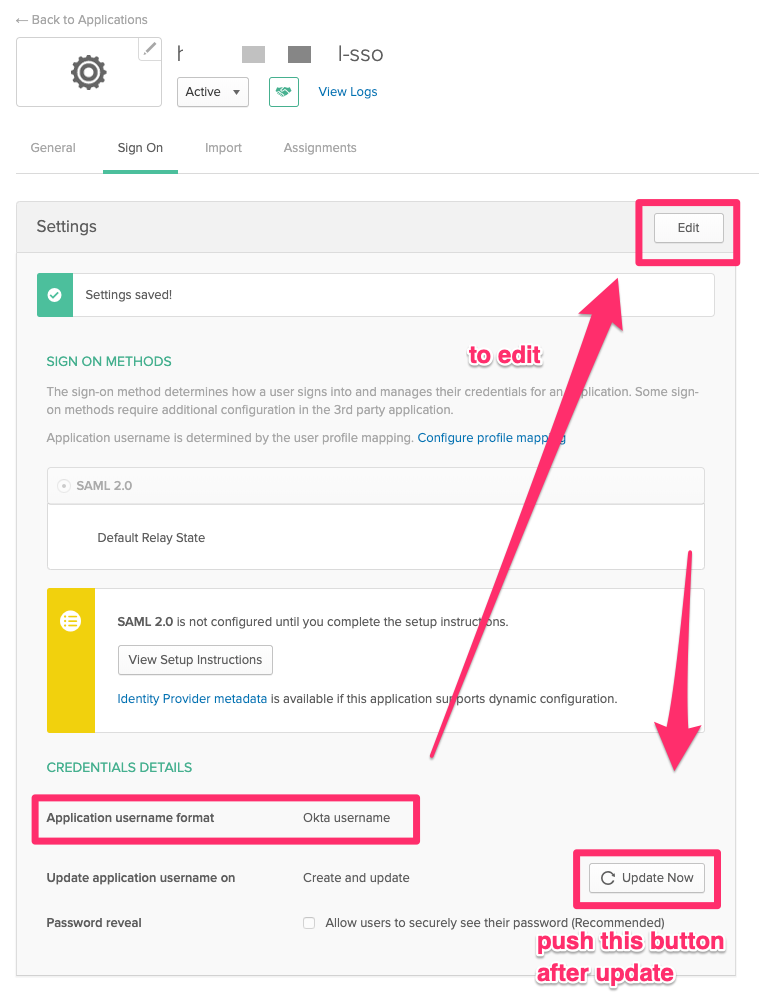
Okta uses Okta username as a default Application username format. The Application username is used as the identifier in TD Console. In TD Console, the default identifier is user email.
You need to ensure that the identifiers in Treasure Data match the Application usernames in Okta.
Select Edit to specify the Application username format in Okta.
Next, you’ll need to open TD Console to verify the same identifiers match.
From TD Console, navigate to Control Panel > Users.
Select the name or the Profile icon of the user.
Select Details to specify a user’s unique identifier in TD Console.